A couple weeks ago, Microsoft released the MS16-063 security bulletin for their monthly Patch Tuesday (June 2016) security updates. It addressed vulnerabilities that affected Internet Explorer. Among other things, the patch fixes a memory corruption vulnerability in jscript9.dll related to TypedArray and DataView.
Second paragraph
Theme
We begin with comparing the May and June versions of jscript9.dll in BinDiff:
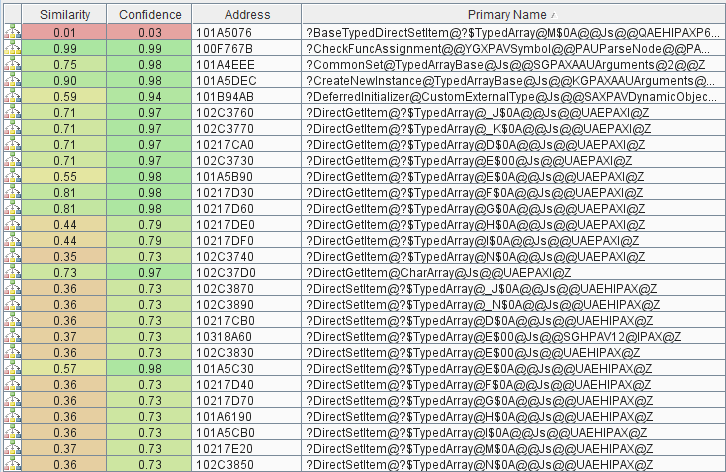
In pseudo-code, it looks like the following:
1
2
3
4
5
6
7
8
9
10
11
inline Var DirectGetItem(__in uint32 index)
{
if (index < GetLength())
{
TypeName* typedBuffer = (TypeName*)buffer;
return JavascriptNumber::ToVar(
typedBuffer[index], GetScriptContext()
);
}
return GetLibrary()->GetUndefined();
}

